COSO objectives refer to the goals of a company. Which fall into three categories: OperationsReportingCompliance Management designs, implements, and monitors internal controls to meet company objectives (goals). Each internal control put into place falls under one of these three objectives. Let’s take a look at each objective to determine which type of control would help an organization meet the objectives. Operations Objective Operations objectives refer to the entity’s business … [Read more...] about Understanding the COSO Control Objectives
Internal Controls
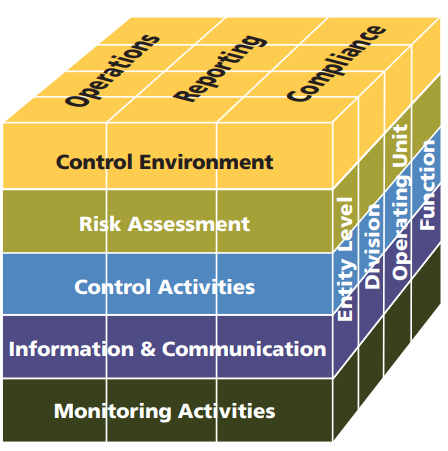
The COSO Internal Control Framework
The COSO framework was developed to help organizations design and implement a system of internal control, enterprise risk management, and fraud deterrence. COSO stands for The Committee of Sponsoring Organizations of the Treadway Commission. History of the COSO Framework In June 1985, the National Commission on Fraudulent Financial Reporting was established. The Commission was commonly referred to as the “Treadway Commission” after its chairman the SEC Commissioner James C. Treadway, … [Read more...] about The COSO Internal Control Framework
How to Create an Effective Whistleblower Policy
A whistleblower policy provides employees and others the opportunity to report questionable activities for investigation. Providing employees with the knowledge of how and where to report, what information to report, how employees will be protected, and how the company will handle investigations. Whistleblowing policies help reduce workplace fraud and shortens the lifespan of fraud schemes. According to The Association of Certified Fraud Examiners (ACFE), whistleblower tips uncovered 43% of … [Read more...] about How to Create an Effective Whistleblower Policy
What is a phishing scheme?
A phishing scheme is conducted typically by email. However, they can occur by a text, an app, or a pop-up window. They claim to have something that needs your immediate attention. Often there is something to entice the user to click on the link or attachment that is included in the email. What would someone be phishing for? The goal behind phishing is to gain access to your computer or device without your knowledge. They are hoping that in some way they can gain access to data that would … [Read more...] about What is a phishing scheme?
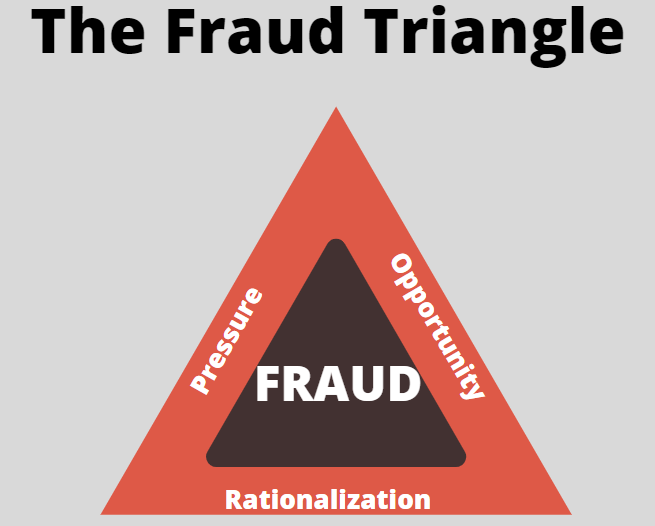
What is the Fraud Triangle?
The fraud triangle helps explain the motivation behind why an employee would commit fraud/steal from their workplace. Three components make up the fraud triangle: opportunity, pressure, and rationalization. When all of these components exist, there is a high likelihood that fraud will be committed. Similarly, this can signal that fraud has already occurred or maybe ongoing. Seldom are frauds committed spur of the moment. Typically, they are deliberately planned and executed. Sides of the … [Read more...] about What is the Fraud Triangle?
Collusion the accounting definition
Collusion is when two or more people or businesses get together and plan to benefit themselves financially or politically. Types of collusion Collusion can come in a variety of forms: Two or more employees work together to circumvent the segregation of duties and commit fraud.Due to management override abilities or authority, an employee may unknowingly be assisting in a fraud scheme.One employee feeds information to one or more non-employees to receive a kick-back.Two or more … [Read more...] about Collusion the accounting definition